Table of contents
Open Table of contents
- Discuss about the definition is IoT
- How IoT works
- Describing - ‘Thing’
- Applications of IoT
- IoT Architecture
- What is an IoT Device?
- Understanding about - Edge Computing
- Edge Computing Device
- Fog Computing and its definition
- Fog Computing Device
- IoT Protocols
- IoT Platform
- IoT Platforms - Important Functions
- ThingWorx IoT Platform
- AWS Webservice IoT Platform
- Azure IoT Platform
- IoT Security
- Summary
Discuss about the definition is IoT
IoT, or the Internet of Things, refers to the network of physical objects or “things” that are embedded with sensors, software, and other technologies to connect and exchange data with other devices and systems over the internet.
How IoT works
IoT works through a combination of hardware, software, and communication technologies which enable physical objects to collect data, communicate with other devices or systems, and perform various actions or tasks.
- Step 1: IoT devices are equipped with sensors to collect data from the physical world and actuators to perform actions based on that data.
- Step 2: Sensors continuously collect data from their surroundings.
- Step 3: The collected data is processed and analyzed either on the IoT device or sent to a central server or cloud-based system for analysis.
- Step 4: IoT devices are connected to the internet using various communication protocols and technologies and these connections enable IoT devices to send data to remote servers or receive commands and updates from those servers.
- Step 5: IoT devices transmit the collected and processed data to a central server or cloud-based platform in real-time depending on the device’s design and purpose.
- Step 6: In many cases, the data is further processed and stored in the cloud.
- Step 7: Users can access the data generated by IoT devices through user interfaces, such as mobile apps, web applications, or dashboards in real-time and interact with IoT devices remotely.
- Step 8: Based on the analysis of data and user preferences, IoT systems can trigger automated actions.
- Step 9: IoT security measures are critical to protect the data and devices from unauthorized access or tampering. Encryption, authentication, and access control are some of the key security mechanisms employed in IoT.
- Step 10: IoT devices may receive firmware updates and patches to improve functionality or address security vulnerabilities. Remote management systems help keep IoT devices up to date.
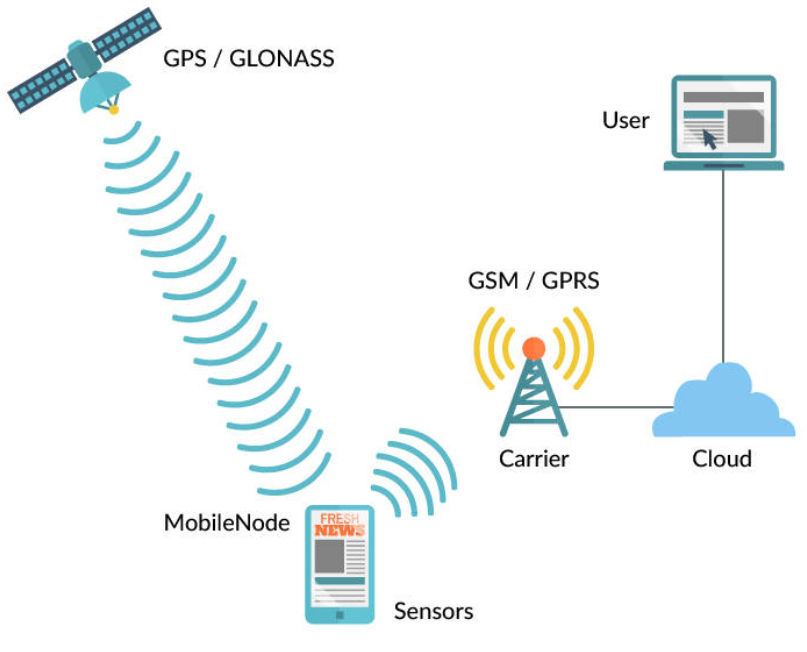
Describing - ‘Thing’
In the context of the Internet of Things (IoT),
a "thing" refers to any physical object or device that is equipped with sensors, software, and connectivity capabilities, allowing it to collect and exchange data with other devices and systems over the internet or a network.These “things” can vary widely in terms of form, function, and application, and they are the fundamental building blocks of the IoT ecosystem.
Applications of IoT
The Internet of Things (IoT) has a wide range of applications across various industries and domains. Below are few examples. IoT continues to evolve with new applications emerging regularly.
-
Smart Homes: IoT devices are commonly used in smart homes to enhance convenience, energy efficiency, and security. Examples include smart thermostats, connected lighting systems, smart locks, and voice-activated assistants like Amazon Alexa and Google Assistant.
-
Healthcare: IoT plays a significant role in remote patient monitoring, healthcare management, and improving the quality of care. Wearable devices like fitness trackers and medical sensors can monitor vital signs, track medication adherence, and send data to healthcare providers for analysis.
-
Industrial IoT (IIoT): In manufacturing and industry, IoT is used for process optimization, predictive maintenance, and real-time monitoring of equipment and machinery. IoT helps reduce downtime and improve overall operational efficiency.
-
Smart Cities: IoT technologies are deployed in urban environments to make cities more efficient and livable. This includes smart traffic management systems, waste management solutions, air quality monitoring, and intelligent street lighting.
-
Agriculture: IoT sensors and devices are used in precision agriculture to monitor soil conditions, crop health, and weather patterns. This data helps farmers optimize irrigation, fertilization, and harvesting processes.
-
Transportation: Connected vehicles and transportation systems leverage IoT to improve safety and efficiency. This includes vehicle tracking and diagnostics, autonomous vehicles, and smart traffic control systems.
-
Environmental Monitoring: IoT sensors are deployed in various ecosystems to monitor environmental conditions such as air quality, water quality, and weather patterns. This data is crucial for climate research and disaster management.
-
Retail: IoT is used to enhance the retail experience through solutions like smart shelves that track inventory, beacon technology for location-based marketing, and customer analytics.
-
Energy Management: IoT devices help manage energy consumption in buildings and industrial settings. Smart meters, for example, enable real-time monitoring and optimization of energy usage.
-
Supply Chain Management: IoT sensors and RFID technology are used to track the movement of goods throughout the supply chain. This helps improve inventory management, reduce losses, and enhance logistics.
-
Logistics and Fleet Management: IoT is used to track and manage fleets of vehicles, optimizing routes, monitoring vehicle health, and improving delivery efficiency.
-
Smart Agriculture: IoT applications in agriculture include precision farming, livestock monitoring, and automated irrigation systems that conserve water and resources.
-
Wearable Technology: Wearable IoT devices, such as smartwatches and fitness trackers, monitor personal health metrics, track physical activity, and provide notifications.
-
Home Automation and Security: IoT enables homeowners to control and monitor their homes remotely, from security cameras and doorbell cameras to smart alarms and locks.
-
Smart Grids: In the energy sector, IoT is used to create smart grids that improve the efficiency, reliability, and resilience of electrical power distribution.
-
Water Management: IoT devices help monitor and manage water resources by measuring water quality, levels, and usage in real time.
-
Asset Tracking: IoT technology is used to track the location and condition of valuable assets, such as shipping containers, equipment, and cargo.
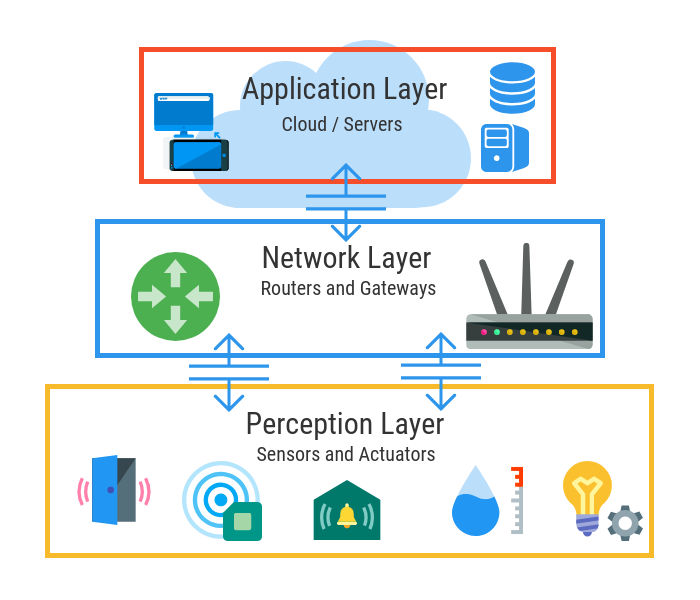
IoT Architecture
IoT architecture refers to the structure or framework that defines how IoT devices, components, and systems interact and work together to collect, process, transmit, and analyze data. IoT architecture typically consists of several layers, each with its own specific functions. IoT architecture design should consider factors like data security, scalability, reliability, and latency requirements to ensure that the system meets the intended objectives and performance criteria.
-
Perception Layer (Sensing Layer):
- IoT Devices/Things: This layer includes the physical IoT devices or “things” equipped with sensors and actuators. Sensors collect data from the environment, and actuators perform actions based on commands or data analysis results.
- Data Acquisition: Sensors collect data from various sources, such as temperature sensors, cameras, motion detectors, and more.
-
Network Layer:
- Connectivity: This layer is responsible for connecting IoT devices to a network, enabling data transmission. Common communication protocols include Wi-Fi, Bluetooth, Zigbee, cellular networks, LoRaWAN, and Ethernet.
- Gateways: IoT gateways are often used to aggregate data from multiple devices, perform protocol translations, and ensure secure communication with the cloud or edge servers.
-
Middleware Layer:
- Data Processing and Analysis: In this layer, data from IoT devices is processed, filtered, and analyzed. This can happen either at the edge (on the device or gateway) or in the cloud, depending on the use case and data volume.
- Security and Authentication: Middleware provides security mechanisms to ensure the integrity, confidentiality, and authentication of data and devices.
- Device Management: Device management services handle tasks like firmware updates, configuration management, and monitoring device health.
-
Application Layer:
- IoT Applications: This is where specific IoT applications and services are developed. These applications can be tailored to various domains, such as smart homes, healthcare, manufacturing, or agriculture.
- User Interfaces: IoT applications often have user interfaces, such as mobile apps or web dashboards, allowing users to interact with and monitor IoT devices and data.
- Automation and Control: IoT applications can trigger automated actions or provide control interfaces for users to manage devices remotely.
-
Business Layer:
- Business Logic: This layer contains the business logic, rules, and workflows that govern IoT operations. It can include data monetization strategies, pricing models, and decision-making processes.
- Integration with Enterprise Systems: IoT data may be integrated with enterprise systems such as ERP (Enterprise Resource Planning) and CRM (Customer Relationship Management) to support business operations.
What is an IoT Device?
An IoT device, short for “Internet of Things” device, refers to
- a physical object or piece of hardware
- is embedded with sensors, software, and communication technology
- enabling it to collect and exchange data with other devices or systems over the internet or a network.
- These devices are a fundamental part of the IoT ecosystem and play a crucial role in various applications across different industries.
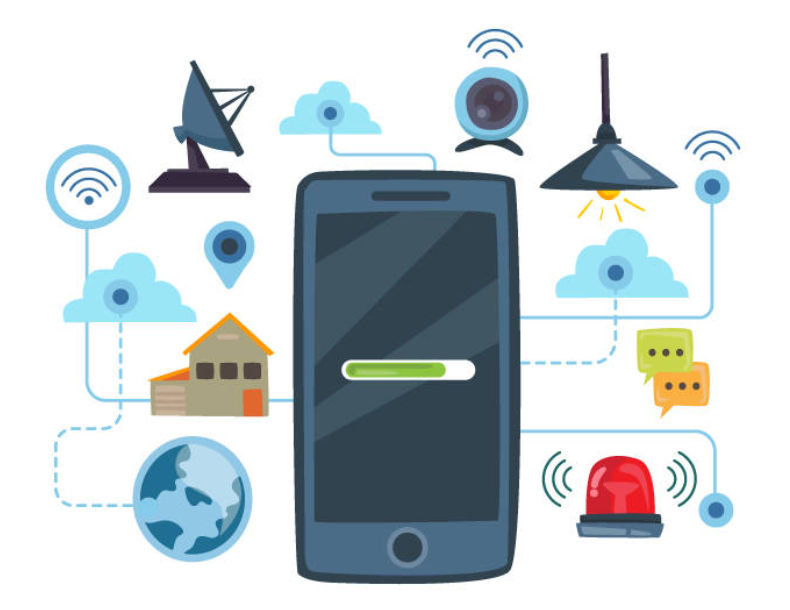
Examples of IoT devices include ~
- Smart thermostats that control home heating and cooling.
- Wearable fitness trackers that monitor physical activity and health metrics.
- Environmental sensors that measure air quality or water quality.
- Connected industrial machines that monitor equipment performance.
- Smart home appliances like refrigerators and washing machines.
- GPS trackers used for asset or vehicle tracking.
- Smart locks and security cameras for home security.
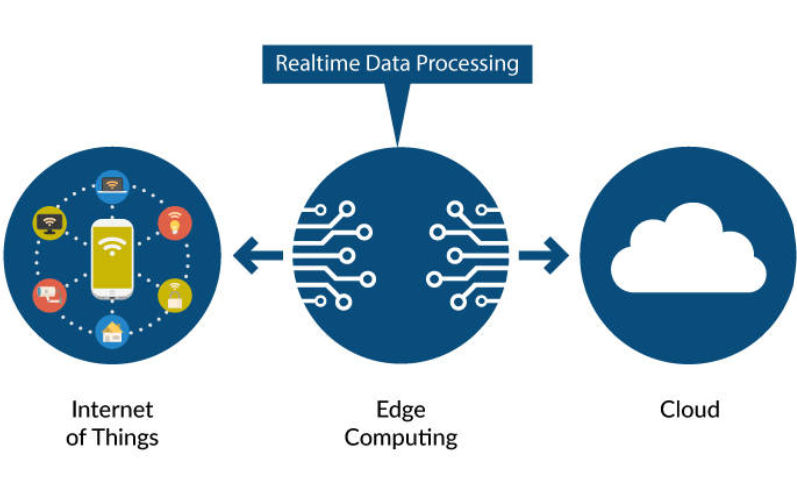
Understanding about - Edge Computing
- Edge computing is a distributed computing paradigm that brings data processing and computation closer to the data source or “edge” of the network, rather than relying solely on centralized cloud-based data centers.
- In edge computing, data is processed locally on or near the device or sensor where it is generated, rather than sending all data to a remote cloud server for processing.
- This approach offers several advantages, including reduced latency, improved real-time processing, enhanced privacy, and more efficient use of network bandwidth.
- Edge computing is seen as a critical component.
- It enables organizations to harness the power of data and analytics at the edge of the network while maintaining the advantages of centralized cloud computing for more extensive data analysis and long-term storage.
Edge Computing Device
In Industrial applications, the Edge computing device is a computing platform designed and developed for a particular application. Its applications vary between high-end computing devices to low-powered devices.
For some of the primary and low-cost applications, the industry prefers to use the following open-source boards to build the Edge computing devices:
-
Raspberry Pi :
- The Raspberry Pi is a low cost, credit-card sized computer.
- It enables people of all ages to explore computing and to learn how to program in languages like Scratch and Python.
- The Raspberry Pi can interact with the outside world and has been used in a wide array of digital maker projects, from music machines and parent detectors to weather stations and tweeting birdhouses with infra-red cameras.
-
Arduino :
- Arduino is a microcontroller-based open-source electronic prototyping board.
Fog Computing and its definition
- Fog computing is a distributed computing paradigm that extends the concepts of edge computing by introducing a hierarchical and more capable layer of computing resources between the edge devices (IoT devices, sensors, etc.) and the centralized cloud.
- The term “fog” is used to describe this intermediary layer, which is closer to the edge devices than the cloud but more powerful than individual edge devices.
- Fog computing aims to address the challenges of latency, bandwidth constraints, and real-time processing, particularly in IoT and edge computing environments.
Fog Computing Device
- In fog computing, the devices that make up the fog computing infrastructure are known as “fog nodes” or “fog devices.”
- These fog nodes are responsible for processing data locally, providing storage, and facilitating communication between edge devices (sensors, IoT devices, etc.) and centralized cloud servers.
- Fog nodes are typically more capable in terms of computing power, memory, and storage compared to individual edge devices, allowing them to handle more complex tasks.
IoT Protocols
The IoT protocols refer to the technology which enables network communication between objects and other internet-enabled devices and the system, using a uniquely identifiable IP address.
IoT protocols are standardized by the international consortium to enable portability, security, and reliability. Some of the famous IoT protocols are MQTT, CoAP, AMQP, 6LowPAN, BLE, ZigBee and LPWAN.
IoT Platform
IoT Platform is a suite of applications that are used to process, prepare, and present data in a meaningful way for creating value/insights to the customers.
IoT Platforms - Important Functions
The five most important functions of the IoT platform are:
-
Device Management - It is a process of managing the list of devices connected to an IoT system. It also helps to manage the device properties.
-
Data Management - It is a method of processing, storing, and deleting data in a given database. It helps to manage data.
-
Security Management - It is a process to enable/protect all things/entities of an IoT system with the necessary protocols/firewalls to avoid or mitigate threats.
-
Network Management - It is a process to manage/enable network connectivity of all things/entities of an IoT system with the protocol standards.
-
Application Management - It is a process of managing/visualizing data in a presentable format to provide insights to the customer.
ThingWorx IoT Platform
- ThingWorx is an industrial Internet of Things (IoT) platform developed by PTC, a technology company specializing in industrial software solutions.
- ThingWorx is designed to enable organizations to develop, deploy, and manage IoT applications and solutions for a wide range of industries, including manufacturing, healthcare, utilities, and more.
- ThingWorx is widely used in various industries to build and deploy IoT solutions that improve operational efficiency, reduce downtime, enhance product quality, and drive innovation.
- It offers a comprehensive set of tools and features to support the entire IoT application lifecycle.
AWS Webservice IoT Platform
Amazon Web Services (AWS) offers a comprehensive Internet of Things (IoT) platform known as the “AWS IoT” suite of services. AWS IoT provides a set of tools and services to help organizations build, manage, and scale IoT applications and solutions securely. AWS IoT is widely adopted in various industries, including manufacturing, healthcare, agriculture, smart cities, and more, to enable IoT solutions that improve efficiency, reduce costs, and drive innovation while maintaining a strong focus on security and scalability.
Azure IoT Platform
The Azure IoT platform is Microsoft’s suite of services and tools designed to facilitate the development, deployment, and management of Internet of Things (IoT) solutions. Azure IoT offers a wide range of services to help organizations connect, monitor, analyze, and control their IoT devices securely. Azure IoT is used across a wide range of industries, including manufacturing, healthcare, agriculture, logistics, and smart cities, to enable IoT applications that improve efficiency, enhance product quality, and drive innovation while ensuring robust security and scalability.
IoT Security
-
IoT helps billions of IoT devices, applications, and services that are connected to each other.
-
All the connected devices need to be protected from threats.
-
Poorly secured IoT devices and services can serve as entry points for:
- Cyberattacks
- Compromising sensitive data
- Weaponizing data
- Threatening the safety of individual users
-
IoT Security is paramount to enable/enhance the advantages of IoT applications.
Summary
IoT has the potential to significantly impact how we live and work by enabling greater automation, efficiency, and data-driven decision-making across various domains. However, it also raises important considerations regarding data privacy, security, and the management of the vast amounts of data generated by IoT devices.